19+ Svg file upload vulnerability ideas in 2021
Home » free svg idea » 19+ Svg file upload vulnerability ideas in 2021Your Svg file upload vulnerability images are available in this site. Svg file upload vulnerability are a topic that is being searched for and liked by netizens today. You can Get the Svg file upload vulnerability files here. Find and Download all royalty-free photos.
If you’re looking for svg file upload vulnerability pictures information connected with to the svg file upload vulnerability topic, you have pay a visit to the ideal blog. Our website frequently provides you with suggestions for seeking the maximum quality video and picture content, please kindly search and locate more enlightening video content and graphics that match your interests.
Svg File Upload Vulnerability. Uploading files by web application users creates many vulnerabilities. When shown as image this is safe because browsers will not execute the script code. A file upload point is an excellent opportunity to execute XSS applications. File upload XSS Vulnerabilities.
![]() File Upload Icon 88986 Free Icons Library From icon-library.com
File Upload Icon 88986 Free Icons Library From icon-library.com
Similarly an html page uploaded as a file could be abused in the same way. I found this vulnerability in the profile picture upload as well as in the CV upload functionality of an application So I was testing in the application and I saw file upload functionality I uploaded a random picture and intercepted it in Burp I looked at the POST request to upload my image I replaced it with an SVG and Content-Type to imagesvg. A file upload point is an excellent opportunity to execute XSS applications. A typical file type which uses XML is SVG. The WordPress Elementor Page Builder plugin 4 million installations was prone to a broken access control vulnerability affecting version 297 and below that could lead to stored XSS vulnerability via SVG image upload. Then select manage profile.
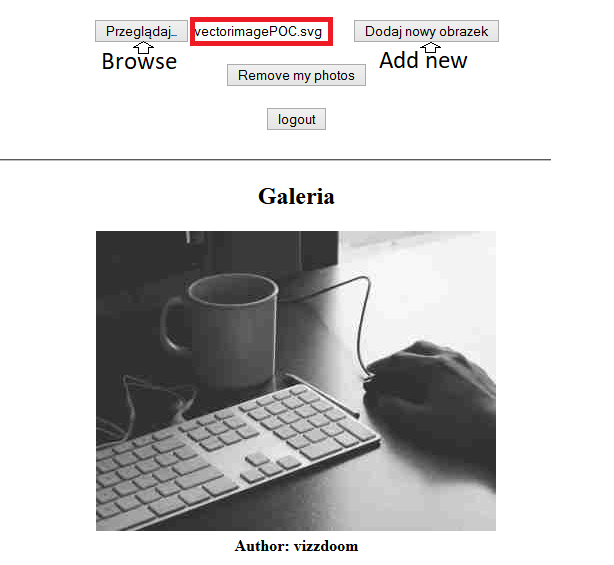
You can upload the following SVG profile picture to achieve XXE.
Visit the vulnerability menu inside DVWA lab to select File Upload. Elementor has an option to allow SVG uploads. A Contributor could upload a specially crafted SVG image containing scripting code. If you are trying to reproduce the vulnerability on the live server then you need to run netcat server on the publically available system and change the xlinkhrefhttp1270011234 to the xlinkhrefhttpYour_publically_Accessible_IP1234 in the SVG file. An attacker can take advantage of this functionality and upload executable codes in file formats such as PHP file JavaScript and exe which could attack client machines or the network by uploading viruses worms or trojan horses. Uploading a file with or as its name.
 Source: research.securitum.com
Source: research.securitum.com
This is what is known as file upload vulnerability. Hello everyone in this blog I will describe how I was able to find XXE that leads to SSRF via a file upload. Then add the image to the image collection with the XSS svg file. You can upload the following SVG profile picture to achieve XXE. There are numerous ways to locate XSS vulnerabilities SVG files are normally overlooked.
![]() Source: icon-library.com
Source: icon-library.com
The directorys path to the uploaded file will show after the upload is successful. Visit the link of the uploaded SVG file. Press Browse and choose the file then press Upload to upload the imgphp on the webserver. How to Look for Stored XSS Using SVG upload. Right click and see the XSS image via the svg file is executed.
 Source: blog.yeswehack.com
Source: blog.yeswehack.com
Hello everyone in this blog I will describe how I was able to find XXE that leads to SSRF via a file upload. Elementor has an option to allow SVG uploads. The directorys path to the uploaded file will show after the upload is successful. This path is the actual location of the uploaded file. A typical file type which uses XML is SVG.
![]() Source: icon-library.com
Source: icon-library.com
I found this vulnerability in the profile picture upload as well as in the CV upload functionality of an application So I was testing in the application and I saw file upload functionality I uploaded a random picture and intercepted it in Burp I looked at the POST request to upload my image I replaced it with an SVG and Content-Type to imagesvg. Uploading files by web application users creates many vulnerabilities. That wouldnt give you XSS even if you an SVG did mean XSS which it usually doesnt. How to Look for Stored XSS Using SVG upload. Many sites have user rights to upload personal data pictures of the upload point you have a lot of opportunities to find the relevant loopholes.
 Source: blog.online-convert.com
Source: blog.online-convert.com
A file upload point is an excellent opportunity to execute XSS applications. Visit the link of the uploaded SVG file. A file upload point is an excellent opportunity to execute XSS applications. File uploads can be vulnerable to XXE if the application parses XML files. There are numerous ways to locate XSS vulnerabilities SVG files are normally overlooked.
![]() Source: icon-library.com
Source: icon-library.com
A file upload point is an excellent opportunity to execute XSS applications. In this functionality pentesters are looking for gaps leading to remote code execution on the server side. These SVG files can contain malicious scripts. I found this vulnerability in the profile picture upload as well as in the CV upload functionality of an application So I was testing in the application and I saw file upload functionality I uploaded a random picture and intercepted it in Burp I looked at the POST request to upload my image I replaced it with an SVG and Content-Type to imagesvg. A Contributor could upload a specially crafted SVG image containing scripting code.
 Source: onappsec.com
Source: onappsec.com
This vulnerability can be used to do all kinds of things from stealing users cookies to bypassing SOP via CORS. A Contributor could upload a specially crafted SVG image containing scripting code. When following a link to this image the code would be executed. Authenticated SVG Uploads Activation. Uploading a file with or as its name.
 Source: en.wikipedia.org
Source: en.wikipedia.org
Exploit XXE with SVG files. When shown as image this is safe because browsers will not execute the script code. What if the upload of a new file resulted in the execution of a malicious JS script. Actually all types of uploaded file are vulnerable to this albeit not in such a direct easy-to-exploit way. Visit the vulnerability menu inside DVWA lab to select File Upload.
 Source: en.wikipedia.org
Source: en.wikipedia.org
- Rhymix CMS should be hosted on your local server. This path is the actual location of the uploaded file. In PageKit v1018 a user can upload SVG files in the file upload portion of the CMS. That wouldnt give you XSS even if you an SVG did mean XSS which it usually doesnt. Uploading a file with or as its name.
![]() Source: icon-library.com
Source: icon-library.com
Payload save format svg. These SVG files can contain malicious scripts. Similarly an html page uploaded as a file could be abused in the same way. This path is the actual location of the uploaded file. Authenticated SVG Uploads Activation.
This site is an open community for users to do submittion their favorite wallpapers on the internet, all images or pictures in this website are for personal wallpaper use only, it is stricly prohibited to use this wallpaper for commercial purposes, if you are the author and find this image is shared without your permission, please kindly raise a DMCA report to Us.
If you find this site beneficial, please support us by sharing this posts to your preference social media accounts like Facebook, Instagram and so on or you can also save this blog page with the title svg file upload vulnerability by using Ctrl + D for devices a laptop with a Windows operating system or Command + D for laptops with an Apple operating system. If you use a smartphone, you can also use the drawer menu of the browser you are using. Whether it’s a Windows, Mac, iOS or Android operating system, you will still be able to bookmark this website.